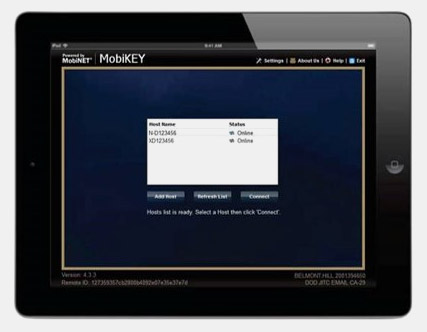
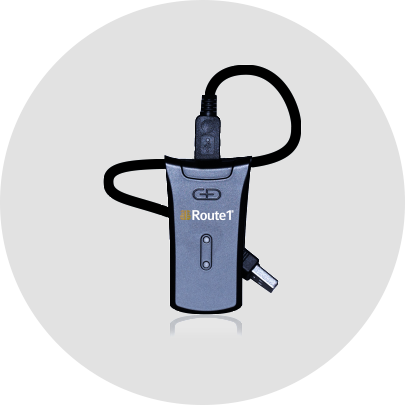
The MobiKEY Classic 2 (MC2) is an identity validation tool that simplifies the access component, while the MobiNET platform universally manages the identities of users and entitlement to digital resources through the MobiKEY application software.
This patented technology is embedded on a smartcard enabled, cryptographic USB device, making it one of the most powerful and easy-to-use multi-factor authentication technologies available today.
Completely clientless and driverless, the MobiKEY device ensures that the user leaves no trace or evidence of their computing session on the Remote asset, while protecting the enterprise network from any viruses and malware. All enterprise files stay within the enterprise firewalls, simplifying security policy enforcement.